Table of contents
As businesses increasingly rely on mobile payments apps like Apple Pay, they are turning to tokenization, which adds an extra level of security to sensitive payment card data. Read on to find out how tokenization works and the benefits of this advanced form of payment security.
What is payment tokenization?
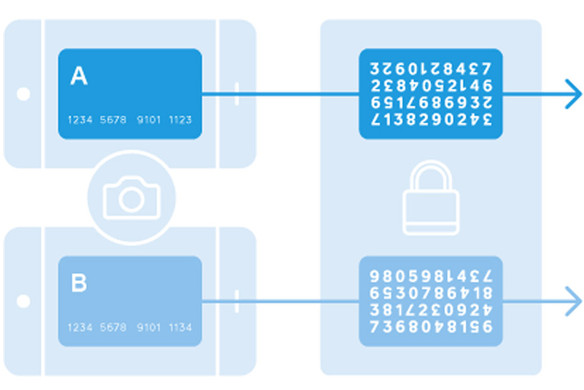
Tokenization is the process of protecting sensitive payment card data by replacing it with an algorithmically generated number called a token. Tokenization is primarily used in finance, payments, and digital assets. In credit card tokenization, the customer’s primary account number (PAN) is replaced with a series of randomly generated numbers, called the token. These tokens can then be passed through the internet or the various wireless networks needed to process the payment without actual bank details being exposed.
Like the nationwide shift to chip cards and contactless payments, tokenization’s end game is to prevent the bad guys from duplicating your bank information onto another card, improving payment security. While chip cards protect against fraud that occurs when someone pays at a physical store, tokenization is primarily designed to fight online or digital breaches.
How does tokenization work?
Tokenization can seem like an indiscernible process when really, a lot is happening under the surface to provide payment security. Here are the steps involved in tokenization:
1. The customer presents their payment card information by entering it online, using a mobile wallet, or tapping/inserting a physical card at a payment terminal.
2. The payment system sends those card details to the payment processor’s token service provider (TSP).
3. The TSP generates a unique token consisting of a random string of numbers. Because it has no mathematical relationship to the actual payment card data, it has no intrinsic value, which renders it useless to fraudsters.
4. The newly created token is sent back to the merchant’s system to replace the actual card data.
5. The token is sent to the payment processor, which forwards the token to the TSP, which retrieves the corresponding actual card data.
6. The actual card information is then used to process the payment through normal authorization channels to the card-issuing bank, which approves or declines the transaction.
7. The merchant receives the authorization response but continues to only see and store the token rather than the actual card data, thus continuing to protect sensitive data. Subscription-based businesses can securely store these tokens for future billing cycles.
What types of businesses implement tokenization for payments?
Essentially, any business that accepts debit or credit card payments from customers can use tokenization for payment security. This includes:
- Ecommerce retailers
- Brick-and-mortar businesses
- Service businesses
- Subscription-based businesses
The benefits of tokenization
Tokenization provides a host of benefits to your business:
- Prevents fraud: By replacing cardholder data with meaningless tokens, businesses dramatically reduce the risk of data breaches. Even if the token’s information is compromised, it cannot be used to conduct fraudulent transactions since tokens have no inherent value outside the specific merchant environment.
- Enhances security for online payments: Ecommerce transactions gain an additional security layer because actual card details never travel over public internet channels, hindering the ability of hackers to target vulnerable payment information during transmission.
- Strengthens recurring billing security: Because businesses can securely store tokens, they can seamlessly rebill for subscriptions or recurring services without the security risks associated with maintaining databases of sensitive payment information.
- Reduces business liability: With cardholder data replaced by tokens, businesses substantially decrease their potential liability exposure in the event of a security incident, protecting both financial resources and brand reputation.
- Promotes customer trust: With breaches escalating, consumers are warier than ever about their personal data falling into the wrong hands. When businesses communicate their use of advanced tokenization technology, customers gain confidence that their financial information is being protected, making them more willing to patronize your business.
Tokenization versus encryption: What’s the difference?
Although both tokenization and encryption protect sensitive payment card data, they employ fundamentally different approaches to security. Encryption transforms sensitive data into unreadable ciphertext using mathematical algorithms and encryption keys, but the original data can be recovered by decrypting the ciphertext with the corresponding decryption key. In other words, the original information still exists — although in a transformed state — and can be seized if decrypted. Some examples of end-to-end encryption are VPNs, Apple’s iMessage feature, and other messaging apps like WhatsApp.
However, tokenization completely removes sensitive data (such as a customer’s bank account details in credit card and eCommerce transactions) by replacing it with random tokens that have no mathematical relationship to the original information. Unlike encryption, there is no algorithm that can reverse-engineer the original data from the token.
Tokenization can be particularly valuable for small to medium sized businesses that likely lack a dedicated security team equipped to create and maintain encryption systems. In fact, tokenization is built right into the Square payment platform, offering you all the benefits of reduced risk and improved customer satisfaction.
Tokenization versus encryption
| Criteria | Tokenization | Encryption |
| PAN data displayed | X | |
| Mathematically reversible | X | |
| Reduces PCI scope | X | |
| Payment flexibility: refunds, chargebacks, recurring payments etc. | x | |
| Rotation of keys required | X | |
| End-to-end security | X | |
| Low-cost per transaction | X | |
| Format fits with legacy credit card fields | X | |
| Centrally managed | X | |
| Established security | X |
Both tokenization and encryption are used to reduce the scope of PCI Compliance by reducing the number of systems that have access to customers’ credit card information. (For a primer on PCI compliance, check out our PCI Compliance Guide.) While both have their places in payment technology, tokenization is fast emerging as a more cost-effective and secure solution to protecting customer card information and reducing the scope of PCI compliance. Unlike data that is encrypted, tokens are not mathematically reversible with a decryption key, and PAN data is never displayed.
How to implement tokenization
If tokenization is an indiscernible process, that actually has much going on beneath the surface, a seller would be the calm exterior while Square solutions does the work behind the scenes. Because tokenization is built into Square’s payments platform, you can conduct business serenely, knowing that Square is protecting your customers’ sensitive payment card data — and your reputation — by handling tokenization and payment authorization.
Tokenization examples
How is tokenization put to use in the payments industry? Three ways. The first is when businesses keep your card on file for subscription billing and recurring payments. The second is on eCommerce sites that offer frequent, returning customers one-click checkouts. And the third, most prevalent use, is within NFC mobile wallets like Apple Pay.
Payment tokenization: An explainer
Here’s how tokenization helps protect you in the following payment scenarios:
Apple Pay tokenization: After you take a picture of your credit card and load it into your iPhone 6 or newer, Apple sends the details to the card’s issuing bank or network, which replaces your card details with a series of randomly generated numbers (the token). That random number is sent back to Apple, which programs it into the phone. This means that the number stored on the phone can’t be extracted into anything valuable to fraudsters.
Tokenization within apps: Say you want to buy something straight from an app on your phone — concert tickets, clothes, books, or whatever. If your phone contains a token, none of these apps have access to your credit card details. Read: Your bank information is locked down and meaningless to fraudsters. Using a tokenized account can also make it easier to check out, as many apps will link directly to your stored shipping information.
Tokenization in eCommerce: Tokenization also helps protect your online shopping activities. You buy a coffee table on Ikea.com, for example. If IKEA has tokenized the card numbers it keeps on file, your information is safe, even if it gets hacked (which it hasn’t). The retailer may never see or store the credit card number, so if someone weasels into the system (like in the Home Depot breach, for example), all the criminal can see is the randomly generated tokens. And here’s something cool: A new token can be generated for each online retailer, so you’ll have a different code at all the places you’ve shopped. So, if a retailer has a security breach, all tokens issued to that website can be disabled without you having to get a replacement card.
In short, tokenization is a complicated topic, but it’s good to know the basics (and if you’re more visually inclined, we made a simple graphic illustrating how it works above). It’s an exciting evolution in keeping every kind of payment more secure.
FAQs about tokenization
Is tokenized data reversible?
Tokenized data is not mathematically reversible unless you have the original key used to create the token.
How are tokens generated?
Tokens can be generated through mathematically reversible algorithms, one-way non-reversible cryptographic functions, or static tables mapped to randomly generated token values.
Does using tokenization make me PCI compliant?
Employing tokenization won’t in and of itself make you PCI compliant, but it’s considered a best practice and can help to reduce PCI DSS scope. You can see the PCI Security Standards Council’s best practices for choosing tokenization providers here. But don’t worry, Square provides an affordable, PCI-compliant solution.
Learn more about how payment processing fees work with Square.
![]()