Have you ever heard of an account takeover? Not the kind where celebrities take over social media accounts to snap photos of their day. I’m talking about the more malicious kind, where fraudsters gain access to your email and password and access your online accounts with bad intent.
Once fraudsters hack into your account, they can get hold of your private information, divert your deposits, or commit credit card fraud. While the Square Secure team performs 24/7 fraud monitoring on your behalf, here are four things you can do to stop fraudsters in their tracks.
How to stop hackers — 4 Ways to Prevent Account Takeovers
1. Create unique passwords.
The most important thing you can do to stop hackers and protect your personal and business accounts from being taken over by fraudsters is to pick unique passwords and then change them regularly.
Here are qualities of a strong password:
- It’s long and complicated.
Eight letters? Fine. Sixteen letters? Even better. With vAriEd CaPitaliZAtiOn and $pec!al ch@r&cters? Great!
- It’s not easily guessable.
Don’t use simple dictionary words, personal things (like your name), or strings that a stranger could predict. I’m looking at you, “password12345”.
- It’s not shared with other platforms.
Whatever you do, do not use the same password for your email and your Square account. Many experts hypothesize that password reuse is the main driver of hacker success. If you have difficulty remembering your different login information, consider using a secure password manager.
- It’s refreshed on a regular basis.
Millions of credentials are compromised every year across thousands of websites. To keep your account protected for the long term, you should try to change your password every 30–90 days.
So, now think about the passwords that you use. Do you follow these best practices? If not, follow these steps to change your squareup.com password.
2. Don’t trust strange websites and email.
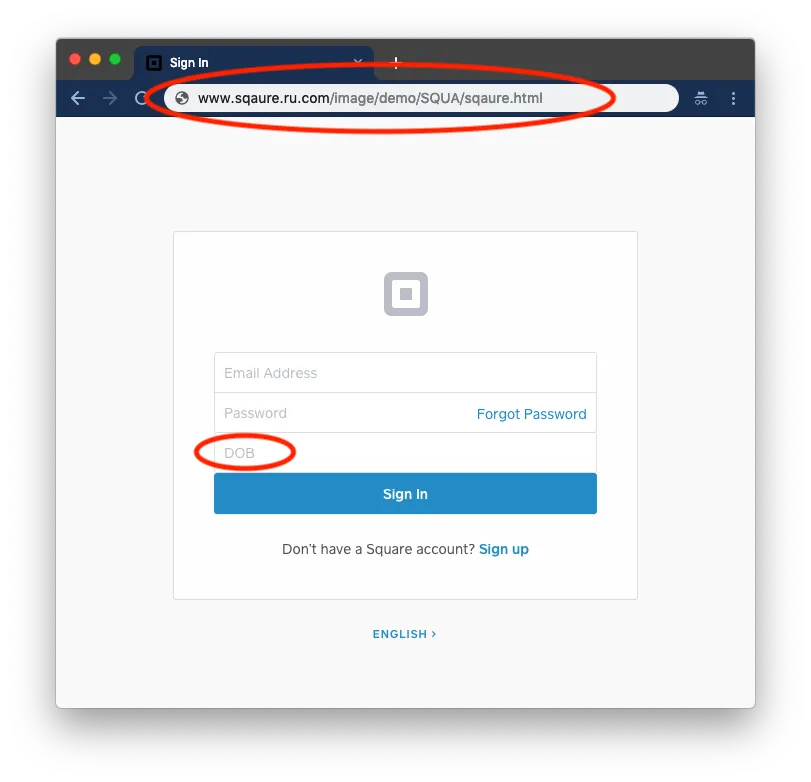
Scammers send phishing email to obtain your private information and use it to commit fraud. These emails are designed to look just like other Square emails in order to trick you, but they are run through third-party websites instead of ours (see the example below).
Whenever a website or email asks you for personal information (e.g., password, Social Security number, birth date, etc.), always verify the request is from someone you trust. This will help prevent hackers from retrieving personal information.
What do you do when when you think that email or website is sketchy? Do not click any links or download any attachments. You may want to forward it to the company it claims to be from. You should definitely mark the message as spam and delete it from your email account.
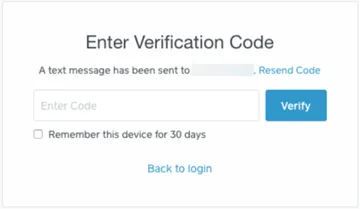
3. Two-step your way to safety.
Two-step verification adds another layer of security to your account, and is a great way to stop hackers. In addition to a username and password to log in, you also need to enter a security code that only you can receive (through either text message or an authentication app).
4. Keep the right checks in place for your business.
Fraudsters are not always sophisticated hackers from far, far away. Sometimes, they are the employees whom you’ve hired. While we’d like to think that rogue employees work with other people at other companies, research suggests that as many as 25 to 40 percent of employees steal from their employers in some way.
If your account gets into the wrong hands, you can have your settings changed, deposits taken, and reputation harmed if fraud occurs. (With Square, you can customize employee permissions to secure the most sensitive information about your business.)
It’s important that you take action to protect your account from takeover and fraud. In addition to adhering to the best practices, above, you should also put a lot of thought into the vendors and partners you work with in your business.
Only work with partners like Square that place as much emphasis on protecting your business and customer data as you do. Look for payment providers, for instance, that offer things like fraud detection, dispute support, and PCI compliance, so if something does happen, you won’t be alone.
![]()